from illegal reuse and IP theft with JavaScript Obfuscator
Both JavaScript code and HTML markup will be protected.
|
|
|
|
|
|
evaluation notes | what is new in current version | Previous versions
Use controls at the right to see how different options affect result of obfuscation; use player-like buttons to navigate between samples and to control playback.
PROTECTION
Identifiers:
Strings:
Comments:
|
||
edition
- Evaluation use only
- Expires in 3 monthes
- Instead of mangling, ReplacementFor_ gets prepended to symbols
edition
- Can be used by only 1 developer
- Does not expire
-
All features are available.
edition
- All developers can use it
- Does not expire
-
All features are available.
More on pricing and licensing terms.
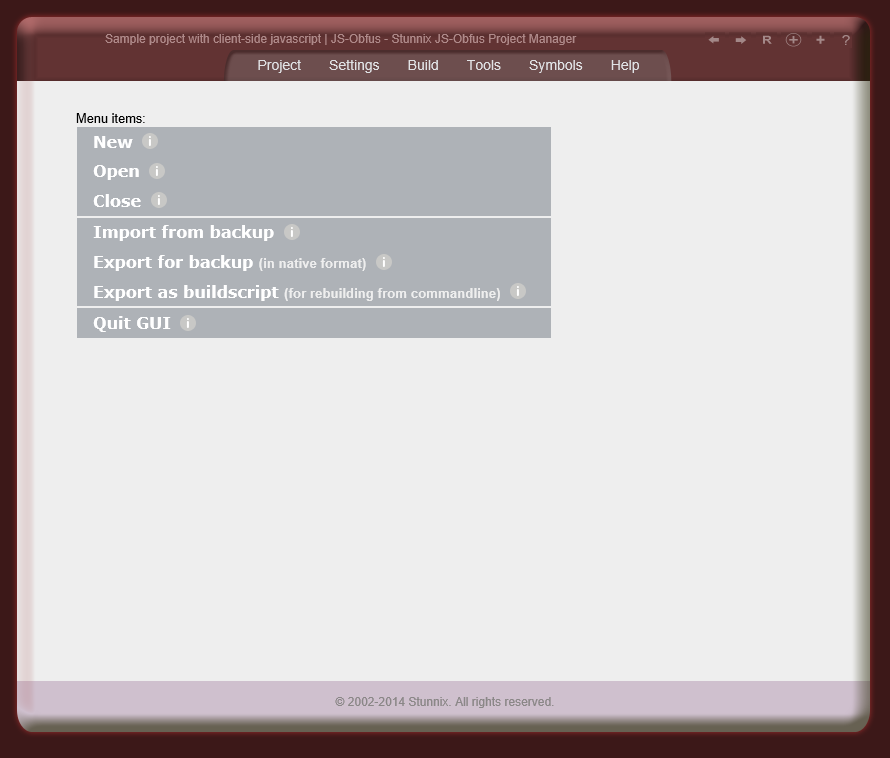
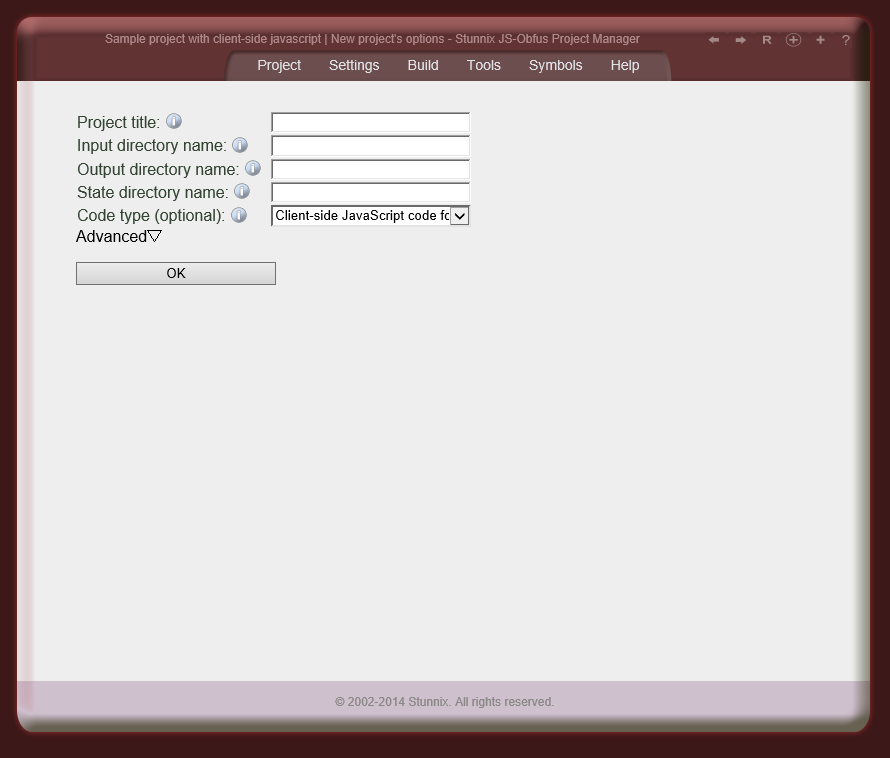
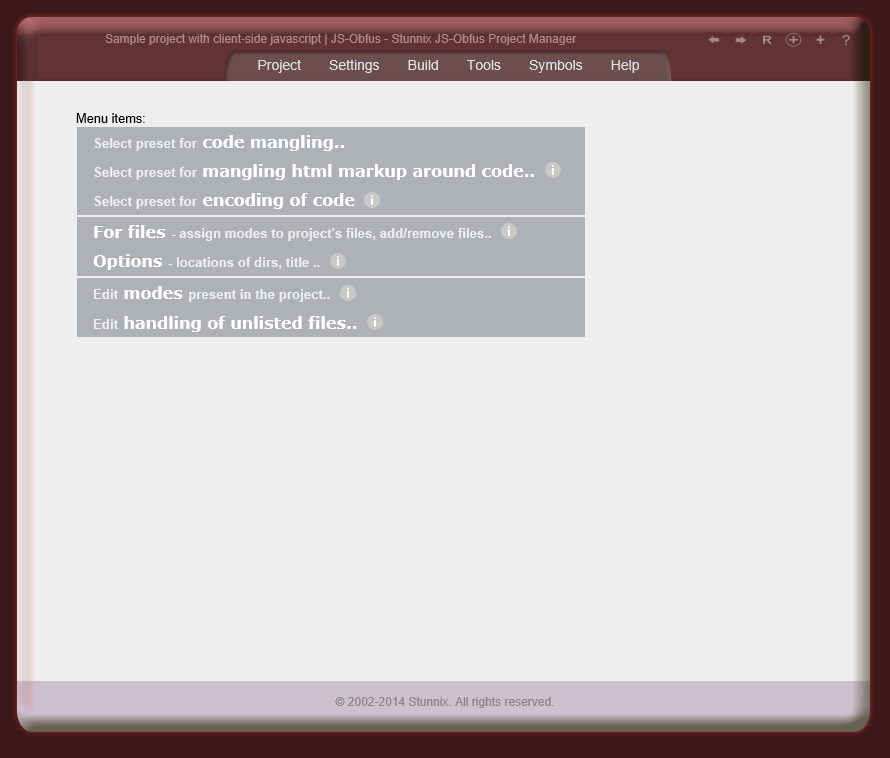
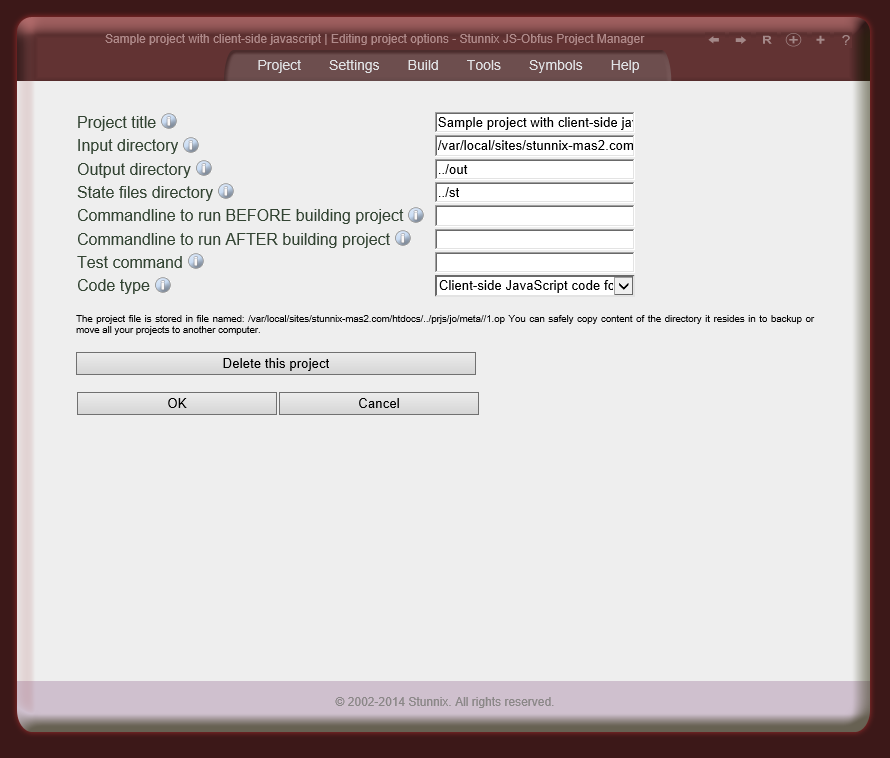
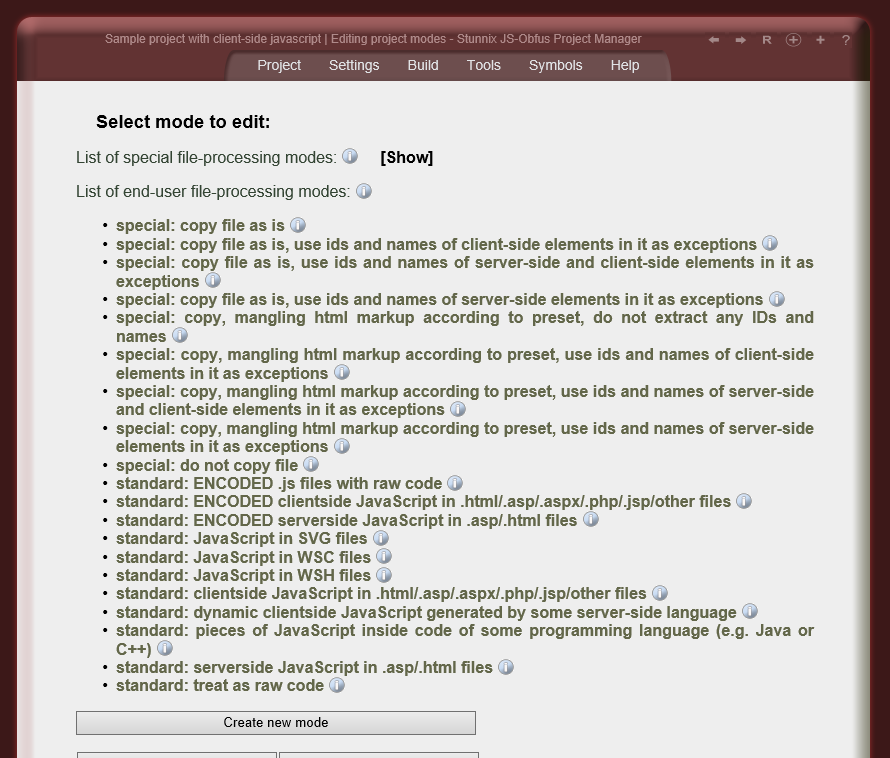
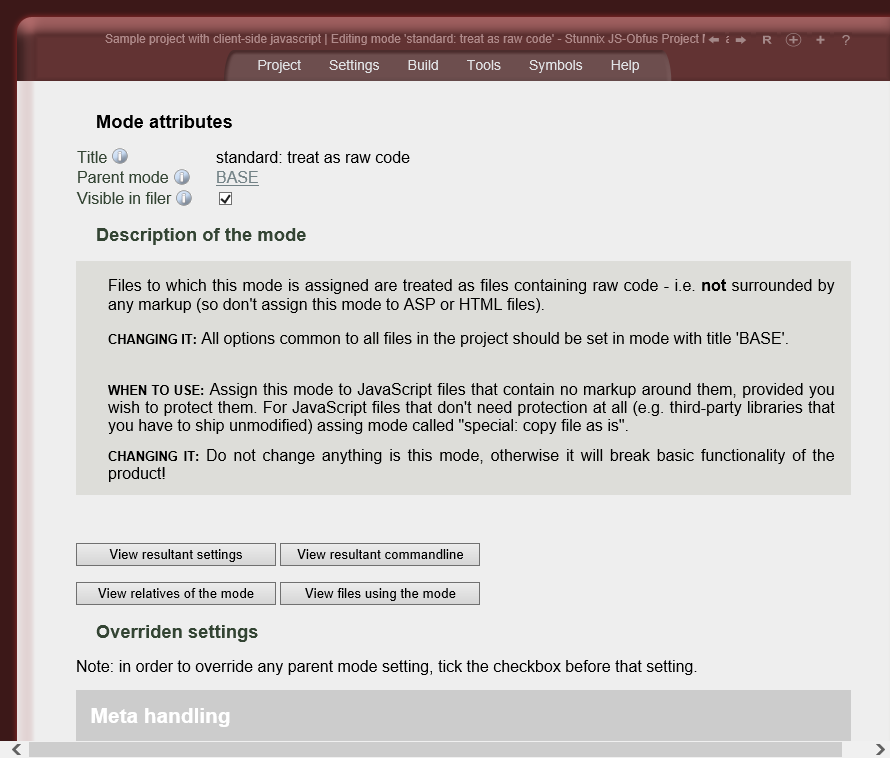
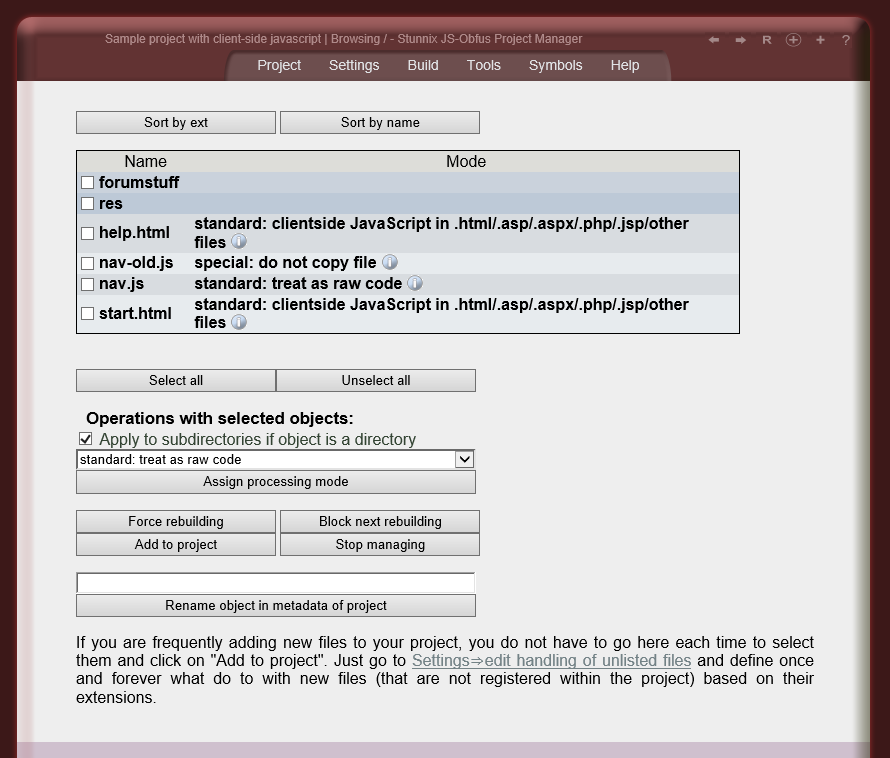
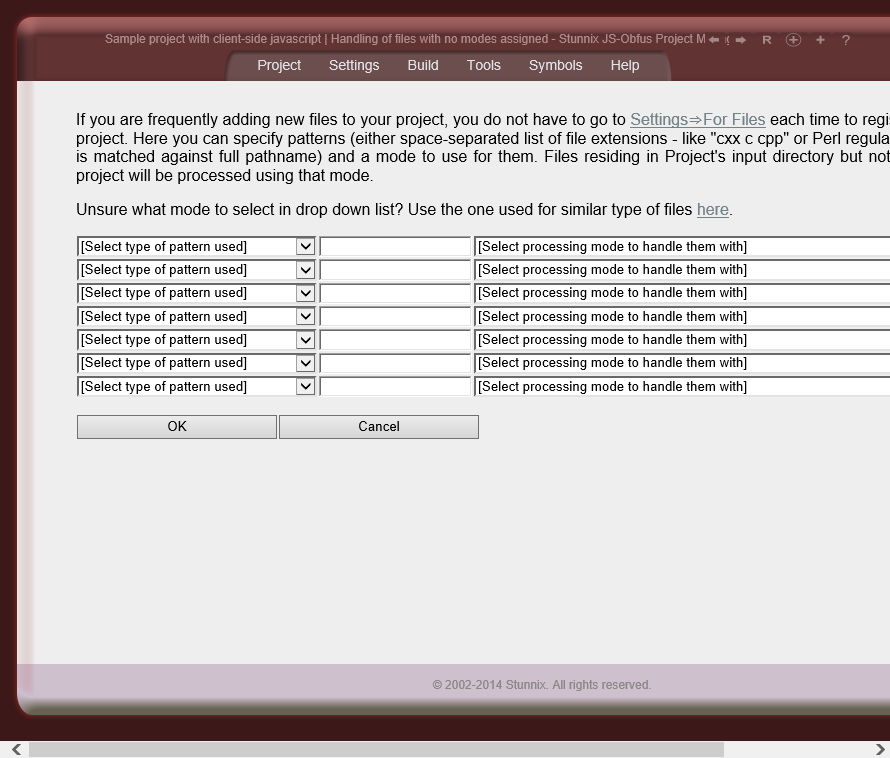
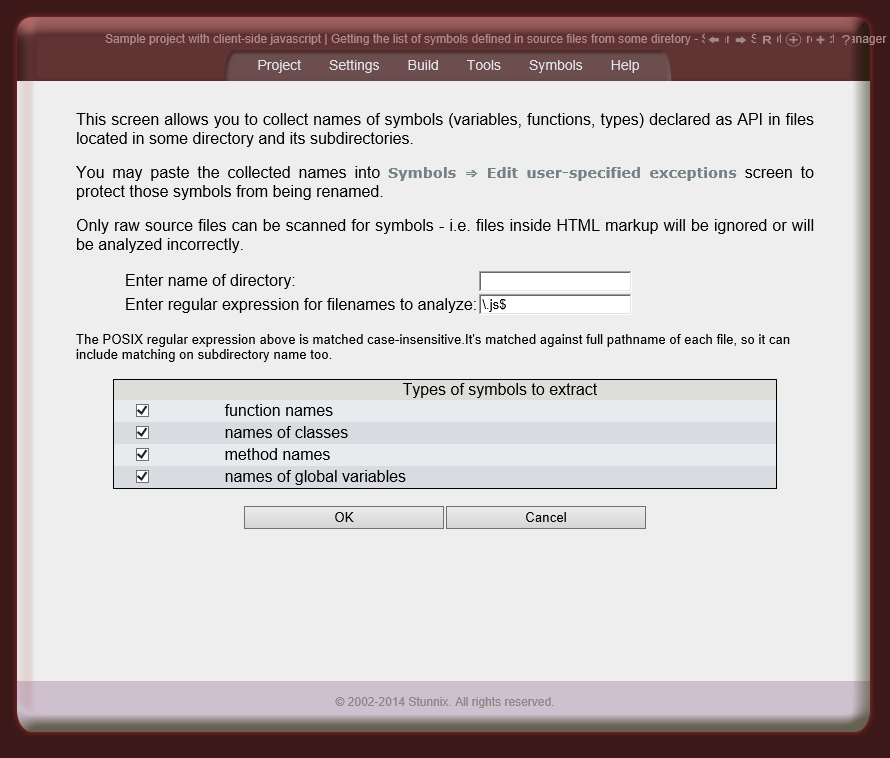
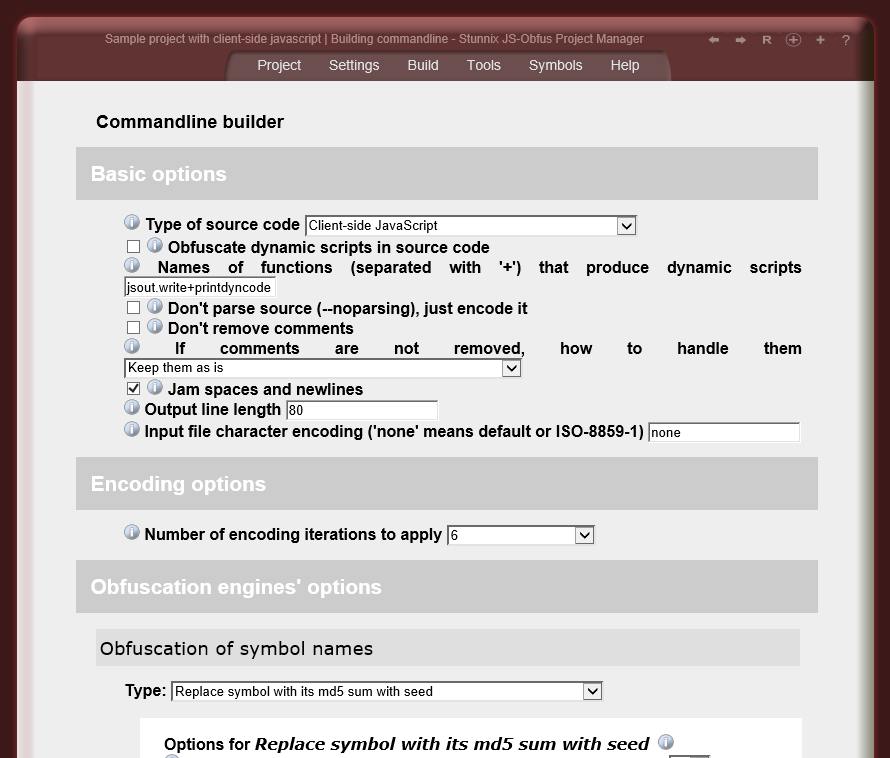
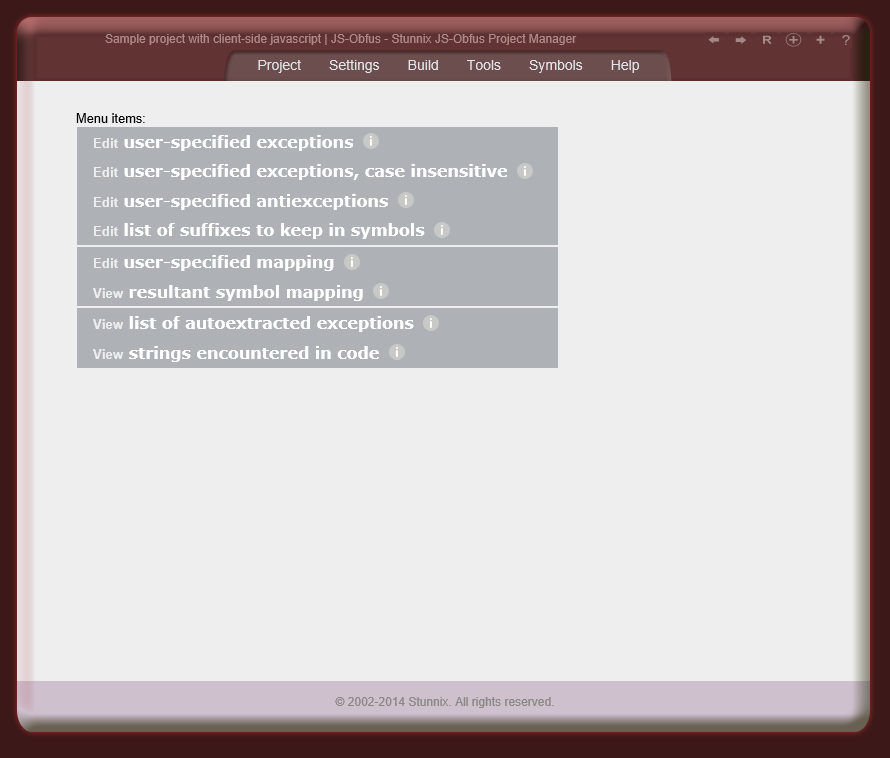
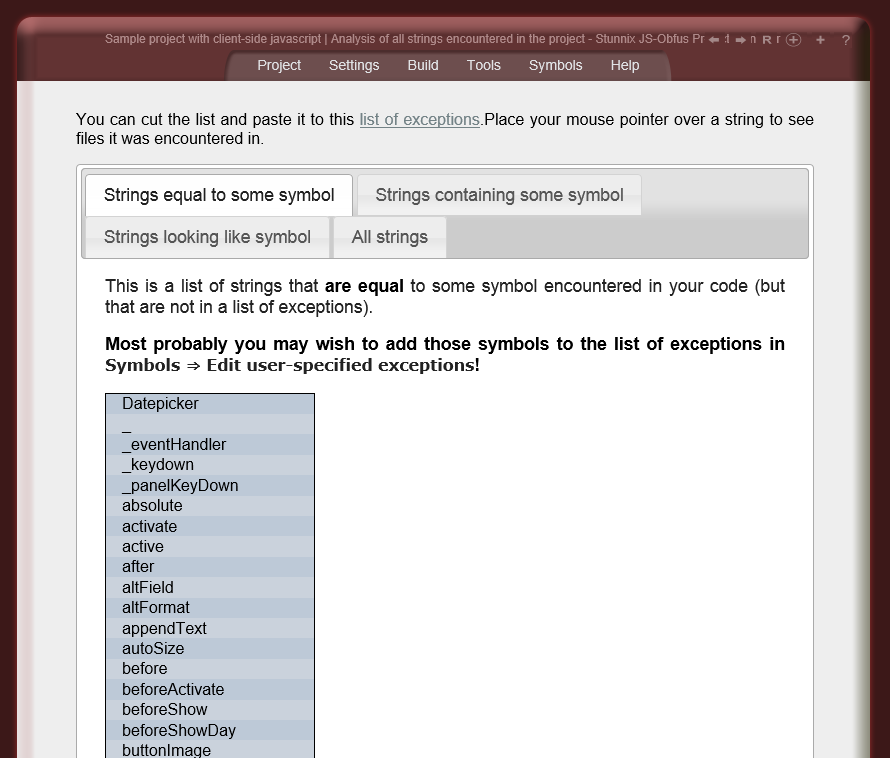
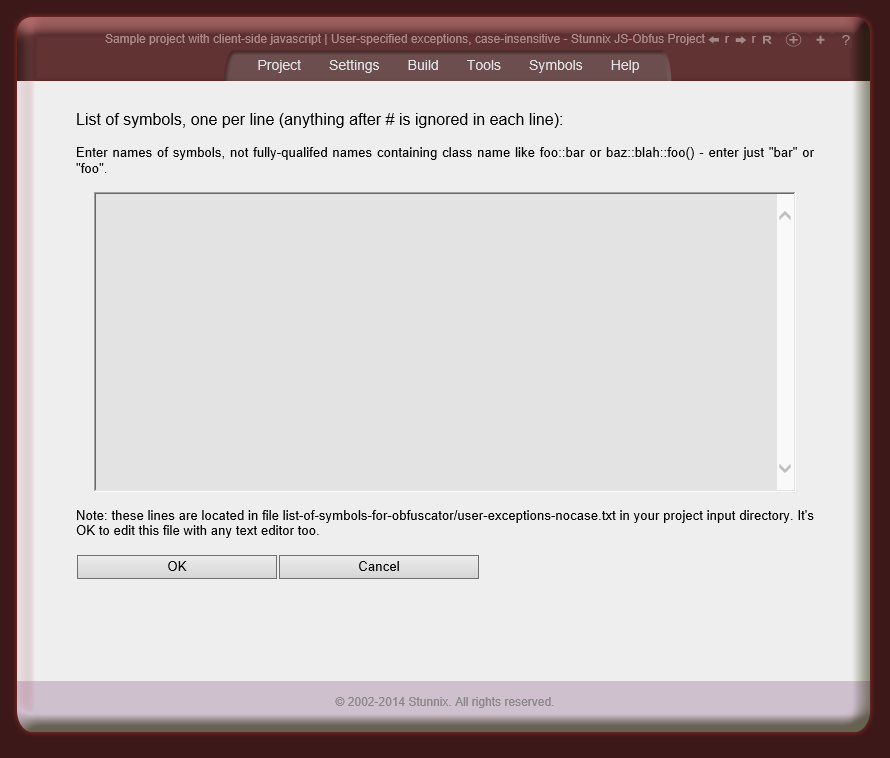
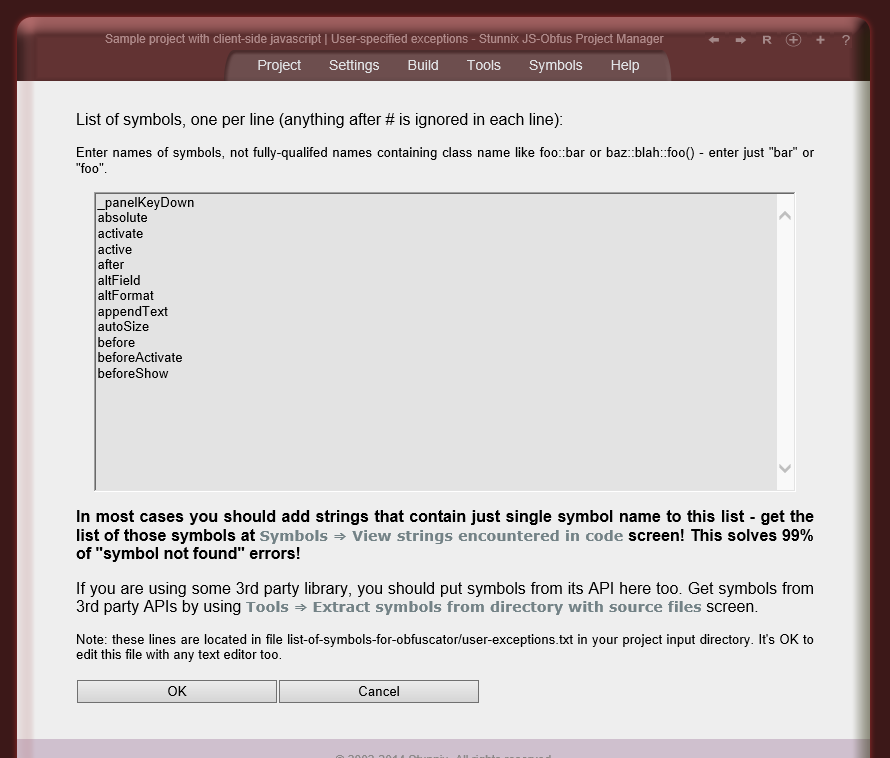
Below are screenshots of Stunnix JavaScript Obfuscator Project Manager GUI. There is a LIVE ONSITE demo of it too!
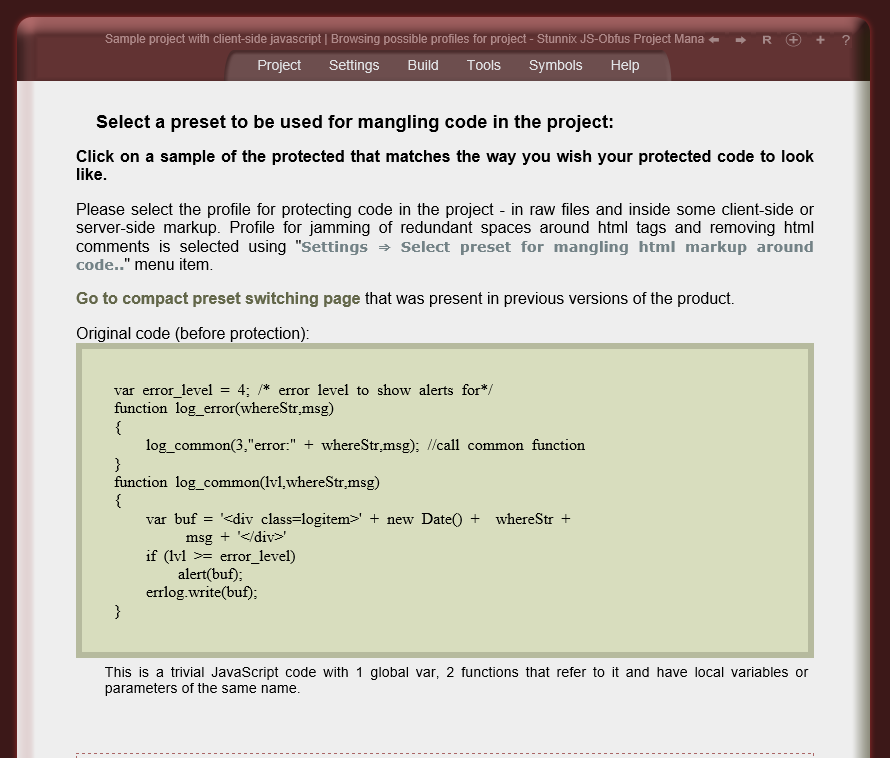
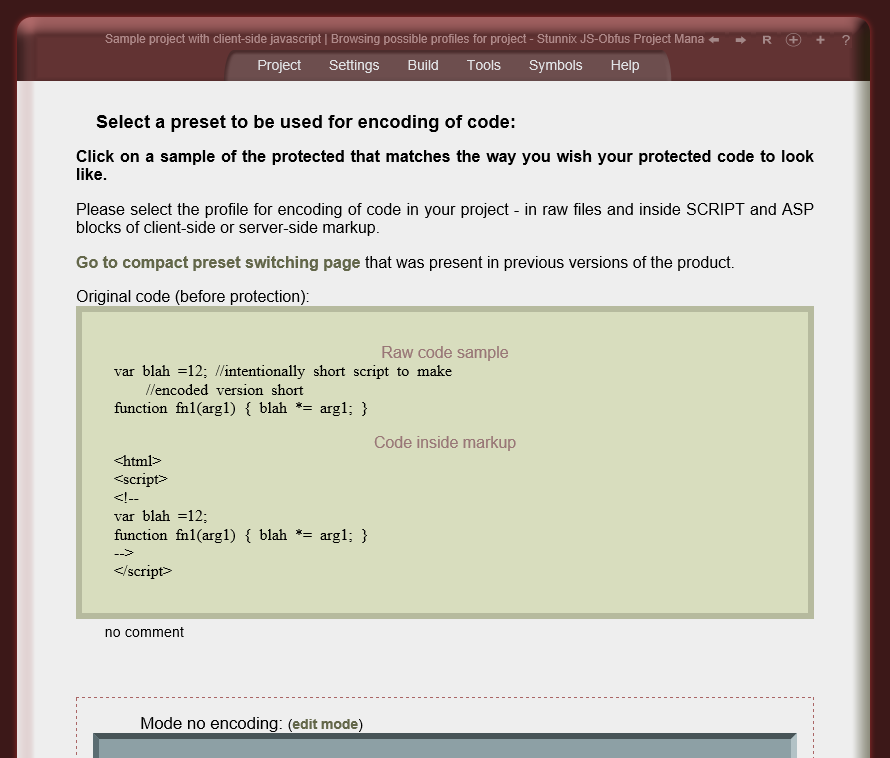
The obfuscation of raw JavaScript code means
Click on the small button "more info" below each item to expand details.
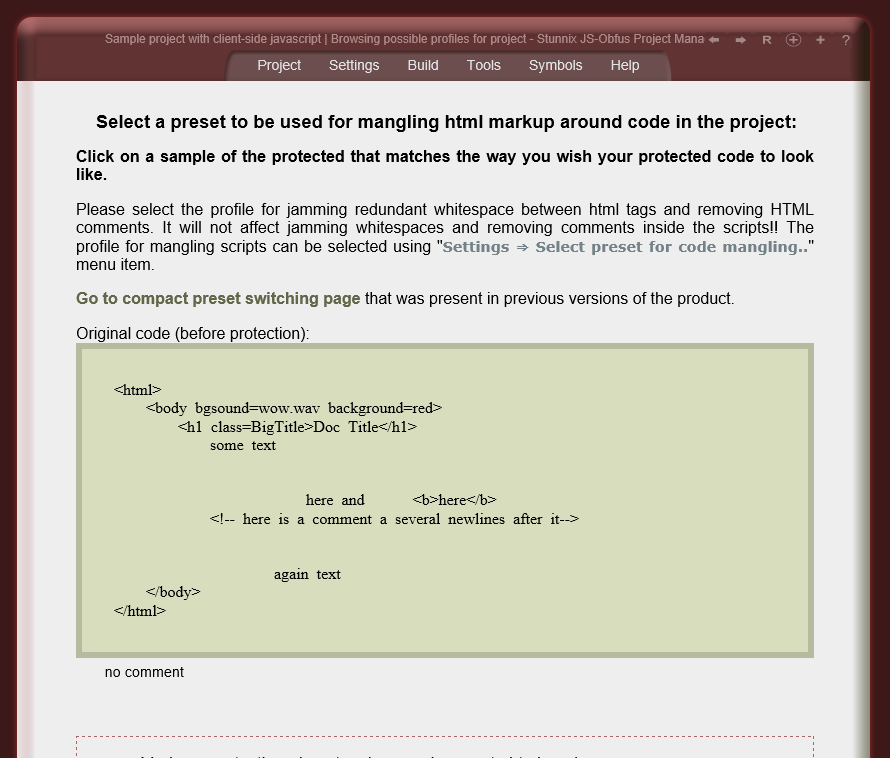
Besides obfuscation of raw JavaScript code mentioned above, the following extra protection is applied to web documents
Click on the small button "more info" below each item to expand details.
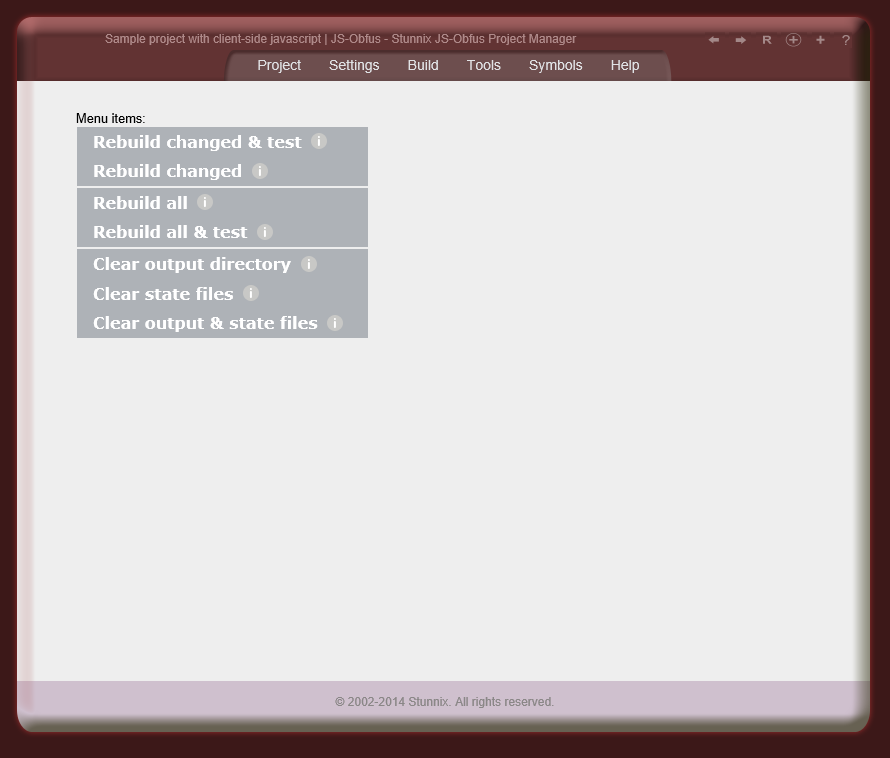
The features summary of JavaScript Obfuscator
Click on the small button "more info" below each item to expand details.